category: News I.S.D.D. plus
During these trying times of the COVID-19 pandemic, when most of us and our colleagues are working remotely from home, I have a constant feeling that something else, beside our remote workforce, is creeping into our network. One threat has always resonated with me – ransomware. Our internal ISO 27000 measures should be adequate to meet such a challenge, but nevertheless I felt the need to put ransomware attacks under scrutiny once again.
Statistics Are Overwhelming
There was once a statistician who drowned in a lake averaging only 5 cm in depth – of course there are many similar jokes about statistics. Joking aside, Coveware claims that the average pay-out for successful ransomware attacks has increased in 2020, up to nearly EUR 100 000. Depending on company size, that is the average amount you should consider investing in preparation for an attack, rather than recovering from the damage done. Once attacked you could also account for 15 days of downtime on average, and even longer for impaired productivity – a substantial amount of time for any business.
 According to IBM Security’s “Cost of a Data Breach Report”, the average total cost of a single data breach in 2020 is EUR 3.27 million. This number includes all sorts of damages and costs, including time and materials to recover production, costs related to company reputation, as well as applicable GDPR compensation. We should be aware that data exfiltration has become an increasingly common component of ransomware attacks. Even though there are still more daunting studies about security breaches (e.g. Comparitech), let me rather outline our recent approach to mitigate ransomware associated risks.
According to IBM Security’s “Cost of a Data Breach Report”, the average total cost of a single data breach in 2020 is EUR 3.27 million. This number includes all sorts of damages and costs, including time and materials to recover production, costs related to company reputation, as well as applicable GDPR compensation. We should be aware that data exfiltration has become an increasingly common component of ransomware attacks. Even though there are still more daunting studies about security breaches (e.g. Comparitech), let me rather outline our recent approach to mitigate ransomware associated risks.
Prepare for the Worst, Hope Not
Luckily for us, most of the knowledge we need to prepare ourselves for such a security threat is already out there, and contained in useful guides which are relatively easy to implement. I like to follow well-regarded materials, such as Gartner’s research paper “Defend Against and Respond to Ransomware Attacks”, to inform my response. As an immediate action, I have concentrated our internal efforts on the first and last phases of defence against ransomware attack, preparation and recovery.
According to Proofpoint, 99% of attacks rely on human input/error, mostly via phishing techniques, to gain access to company infrastructures. This is often via flawed remote desktop services (RDP) that never seem to be patched correctly. Hence, the best course of action for our company was to make sure that all of our access points were handled via single sign-on (SSO) using multifactor authentication (MFA). There is a common misunderstanding that because SSO uses only one set of credentials for authorization, it is a less secure option compared to separate logins across multiple applications. In fact, it is the most effective deterrent against unauthorised access including phishing-type activities.
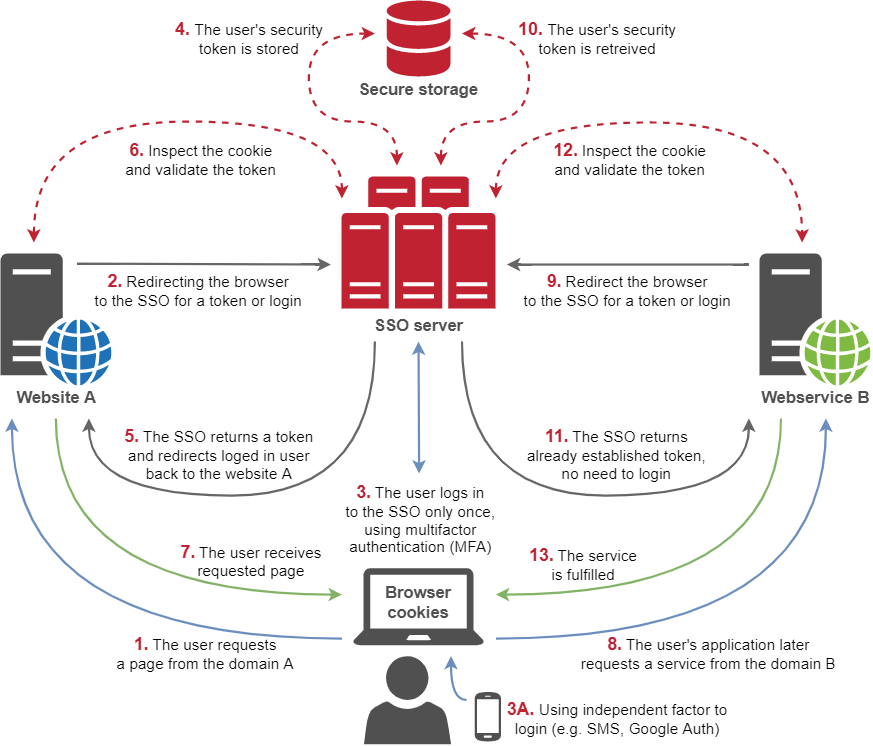
Figure 1. Basic SSO flow
Our own SSO product was already in place, so we only needed to ensure that all of our services were using it. In the end it came down to auditing – every single endpoint deployed to the internet and within our intranet had to be rechecked. In such configurations, SSO needs to have some advanced features, and even handle authentication of machine to machine (M2M) communication flows via OAuth2 and OpenID Connect layer. There were quite a few issues to work through, but at the end of the day all of our services were covered. Priceless – figuratively speaking – my bosses can put the exact number on it. : )
Don’t Put All Your Eggs in One Basket
It is such an old saying, but there is so much truth to it. We may have multi-level backup procedures with segregation protocol, and we can recover all individual assets, but are our disaster recovery plans up to the task when it comes to a full-blown ransomware lockdown? If undetected for a prolonged period of time, malware could be present in the backup of every virtual machine (VM). After backup VMs boot up, files are being decrypted by malware and fed clean via APIs. Hence our routine procedure of restoring and testing a VM’s backup copy would not raise any suspicions, even on compromised machines.
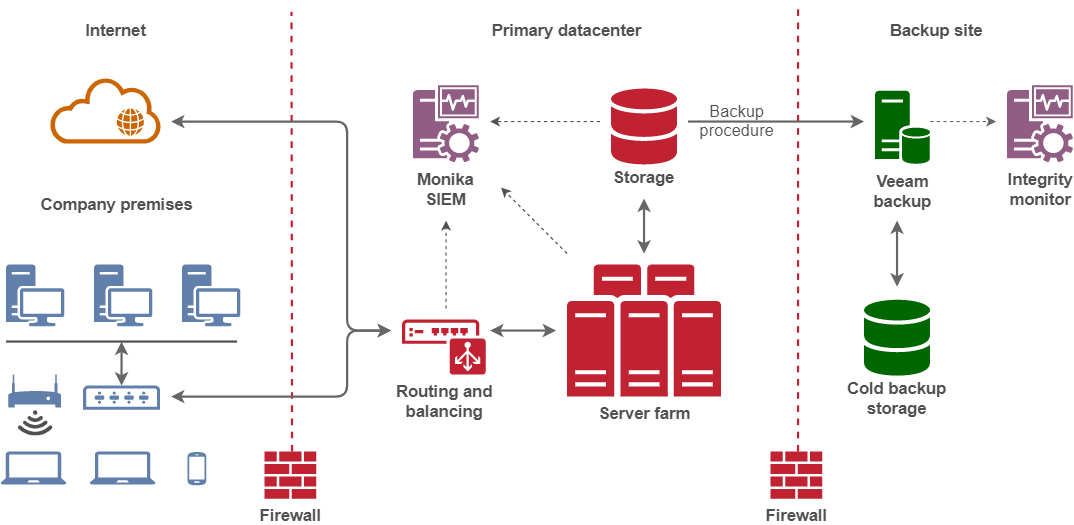
Figure 2. Backup integrity monitoring
There are a few different solutions to this situation, but we usually try to work with what we know and what we have. In this case what we have is Veeam, a powerful backup solution, and Monika, our custom-built security information and event management (SIEM) system. We also decided that if we face a ransomware attack, we would want to discover corrupted or encrypted backups ASAP.
To achieve this goal, we set up a detached monitoring system next to already separated backups. The key lies in using Veeam’s file level restore (FLR) feature to extract logs along with a few signature files. This will effectively feed unprocessed files from cold backup to the monitoring tool without booting up the VM. It is not fully tested yet, but it has had promising results in the sandbox. It should succeed in revealing encrypted files and corrupted VMs.
What’s Next?
It looks like cybercrime is not going away and ransomware attacks will continue to thrive. I do not think that the “bear escape” analogy applies here: “You don’t have to run faster than the bear to get away. You just have to run faster than the guy next to you.” It seems instead to be an endless race to stay one step ahead of the perpetrators. I guess it all comes down to being prepared in limiting the risks you are willing to take on, and planning for the worst, because in IT security it certainly does not matter what you hope for.
I will keep you posted with further interesting developments as they arise.
Rastislav Klč
Chief Security Officer
Rastislav was recognised as the EY ESO Chief Information Security Officer of the year in 2019. He has been with the company since 2011, and has been working as the Information Security Manager since 2014.



